Cryptocurrencies and decentralised finance are built on the notion of shared control and promoted security. They work on distributing power among users by avoiding working through centralised authority and enforcing secure practices by undisclosing users’ identities.
However, illicit actors have exploited these fundamentals to conduct illegal activities and cyber fraud. Breaches and hacks are crypto’s major concerns, where hackers embezzle funds from crypto wallets or hijack a money transfer and divert it in their direction.
It was reported that $3.8 billion worth of cryptos were stolen in 2022 by crypto hacks through various pig butchering scams, bridge attacks, rug pulls or the latest sandwich attack.
Today, we will shed some light on one of the dangerous hacking tactics which Vitalik Buterin warned us about in 2018: DeFi sandwich attacks.
What is Sandwiching?
A crypto sandwich attack entails surrounding a single transaction with two malicious transactions that aim to discredit the victim’s trade from any profits.
This attack is carried out by locating a pending transaction in the mempool of a blockchain and placing one purchase before it and another one after it. These are called front-running and back-running while having the victim’s transaction in between, “sandwiching” it.
The aim of this attack is to manipulate the market’s dynamics, especially through decentralised exchanges and DeFi platforms. Therefore, a sandwich attack does not involve hacking in terms of breaching the code or infiltrating the blockchain system but relies on market manipulation.
The attacker (front run) buys the same token/crypto of the original transaction before it gets validated, which causes that coin value to increase, the victim’s transaction gets processed at a higher price, and then the attacker (back run) sells the token at a higher price and gain the difference as a profit.

How Does a Crypto Sandwich Attack Happen?
Mempool is the blockchain’s list of pending transactions. Basically, it means that validating nodes (miners) have not picked it up and validated it yet for some reasons, including that the gas fees are not high enough.
Some users aim to get the lowest gas fees when they purchase a cryptocurrency, so they get their transaction in the mempool, hoping for it to go through once fees drop.
However, the mempool is publicly shared, and anyone can see the pending list. Attackers can locate a target transaction and front-run a new transaction at a higher transaction cost to motivate miners to validate it first.
This makes the purchase price higher and raises the expected execution price, which makes the desperate victim of crypto fraud receive fewer coins because the transaction becomes more expensive after an unexpected price slippage.
Afterwards, the second layer of the sandwich comes, back-running a sell order at the new higher price and gaining some profits.

Financial Considerations Behind a Sandwich
This type of attack differs from flash loan attacks or rug pulls. However, it aims at having financial gain at the expense of an innocent crypto user.
It is not easy to pull out a successful sandwich attack because of the costs associated with conducting these transactions. The scammer has to pay transaction costs for two purchases, besides the fact that this market manipulation changes the prices by small fractions.
Therefore, attackers are more likely to repeat this trick multiple times before they land a beneficial breach or carefully search the mempool to find the right catch.
Types of DeFi Sandwich Attacks
Sandwich attacks are hard to predict and can happen at any moment since decentralised exchanges attract more users. Having numerous amount users on the platform may lead to more sandwich attacks in DeFi in two ways.
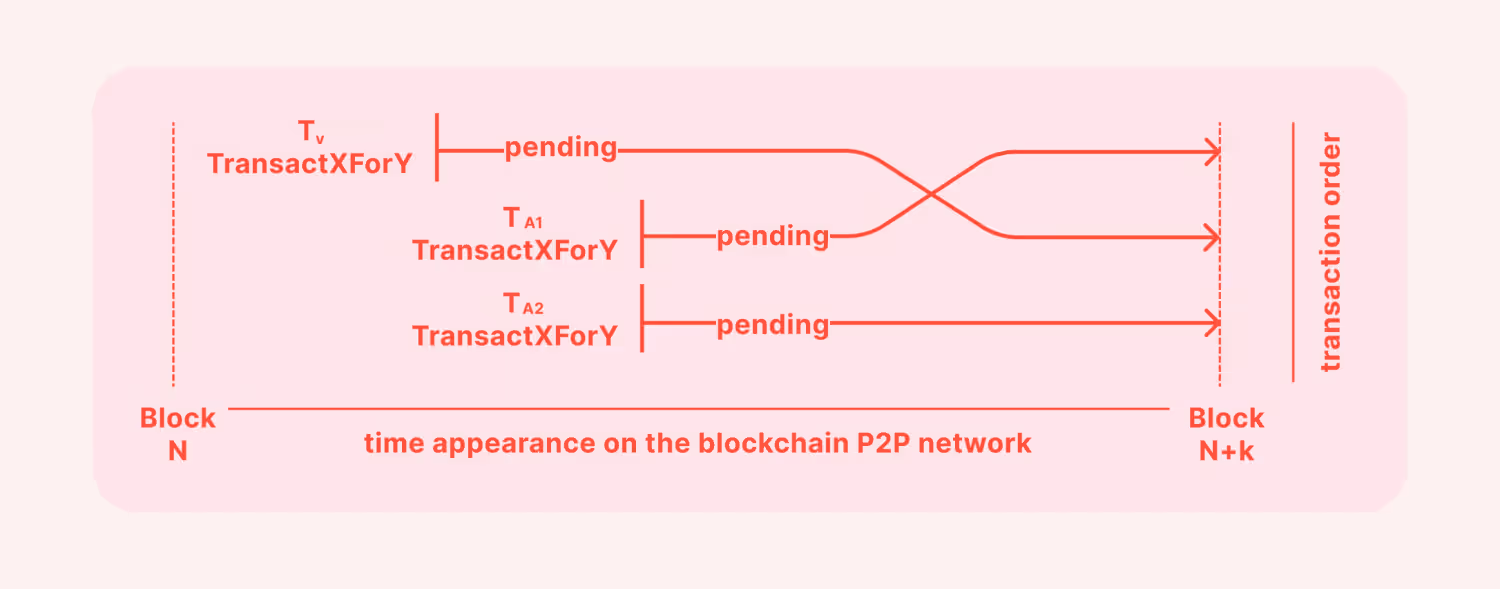
Liquidity Taker vs Taker
This is where liquidity takers attack each other by locating a pending transaction with a substantial amount that can lead to financial gain to front and back run it.
This sandwich attack takes advantage of automated market makers’ standards where the liquidity pool adjusts itself to cope with changing demand and supply dynamics.
Therefore, the subsequent transactions aim to manipulate asset prices and put the original purchase process at a disadvantage, where they received fewer coins/tokens at the end.
However, there is no guarantee that the miner will pick up the malicious transaction first and validate it prior to the victim’s, so there is a chance for sandwich attacks to fail.
Liquidity Provider vs Taker
Another type of sandwich attack is when liquidity providers attack market participants, taking advantage of their ability to change market liquidity and causing an unexpected slippage rate.
This approach works similarly to the aforementioned Taker vs. Taker sandwich attack. However, the malicious actor here undertakes one more step while manipulating liquidity.
Firstly, they remove liquidity from the market to trigger an unexpected price slippage for the victim, whose trade is now different from the expected execution price.
After the victim’s transaction goes through, they re-add liquidity, returning to the initial pool balance before taking an opposite swipe to the original user’s operation to make money on the price difference.

Market Dynamics Causing a Sandwich Attack
Sandwich attacks happen by exploiting the automated market makers exchanges like Uniswap and PancakeSwap because their mechanism involves rebalancing the liquidity pool after demand and supply changes.
Therefore, sandwich attacks are more likely to happen on these platforms and take advantage of the market dynamics. Otherwise, a slippage would not happen, and sandwich attacks would be worthless.
The other factor that makes sandwich attacks work is the price slippage aspect, which happens when the actual execution price is different from the desired price.
This event happens when market liquidity changes dramatically or the asset balance fluctuates because of changes in supply level.
Avoiding Sandwich Attacks in Crypto
Unfortunately, there is no way to evade sandwich attacks in DeFi when they happen because they are done within a few seconds after locating prey pending transactions. Additionally, scammers can continue pulling sandwich attacks without repercussions.
However, there are some precautionary measures that you can take, such as transacting via platforms that ensure low slippage or provide minimum slippage insurance. These platforms deploy special mechanisms to mitigate the chance of sandwich attacks.
Another step you can take is to pay a higher transaction cost to get your purchase processed faster by validating nodes.
Conclusion
Sandwich attacks in decentralised finance take advantage of market dynamics by surrounding pending transactions with two malicious transactions. This approach leads to market imbalances and an unexpected slippage rate.
DeFi sandwich attacks aim at increasing the victim’s trade’s exchange rate and reverse it afterwards to gain financial benefits. These attacks happen between liquidity takers in the market or from a liquidity provider to a taker.
This AMM scam aims at decentralised exchange platforms and protocols since they attract a large number of users, increasing the number of possible sandwich attack victims.



.svg)






