The modern cryptocurrency space is a set of innovative spheres that have developed robustly thanks to the advantages of distributed ledger technology.
On the one hand, this has contributed to the radical transformation of many familiar processes. However, on the other hand, it has created an excessive interest in fraudulent and criminal organisations in users’ personal and financial data to extort, steal or launder money. In turn, this has given rise to the creation of many schemes to accomplish this, the most popular of which is called Doxxing.
This article will help you understand the doxxed meaning in crypto and how this scheme works. Ultimately, you will learn a few practices that will help you protect yourself from this phenomenon.
Key Takeaways
- Doxxing is finding and publicly publishing personal information about a person with malicious intent.
- Doxxing involves a hacker (doxer) who analyses information about a person posted on the Internet to identify that person and then blackmail them.
- Doxing uses different tactics to accomplish its goal, such as hacking, phishing, and sniffing, among others.
What is Doxxing in Crypto Niche?
So, what is doxxing in crypto? Doxing is the process of revealing online identifying information of an individual trader or investor, crypto organisation or company to discover personal and private information that can be used to inconvenience, discredit, extort, coerce and harass the victim using various doxing tools.
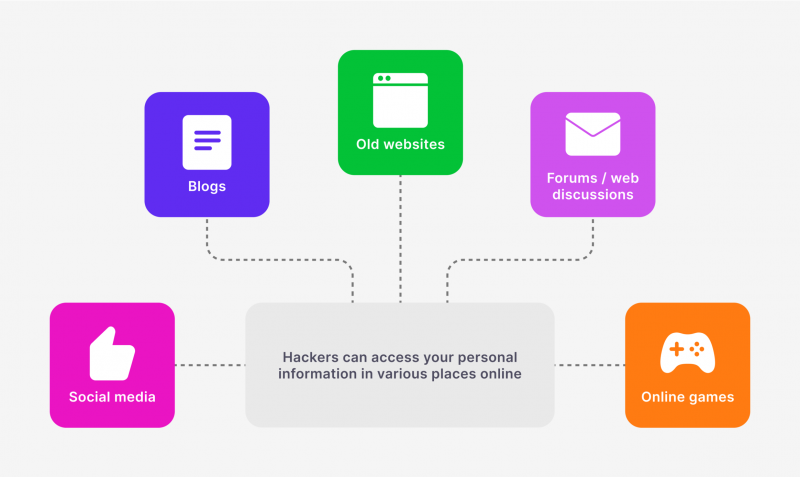
Doxing includes a set of measures to collect information about a subject in social networks, forums, and chat rooms. Data from different sites is compared, analysed, and refined to find blackmail material. In addition to collecting publicly available information, hacking, social engineering, phishing, and other techniques may be used, particularly to extract financial data.
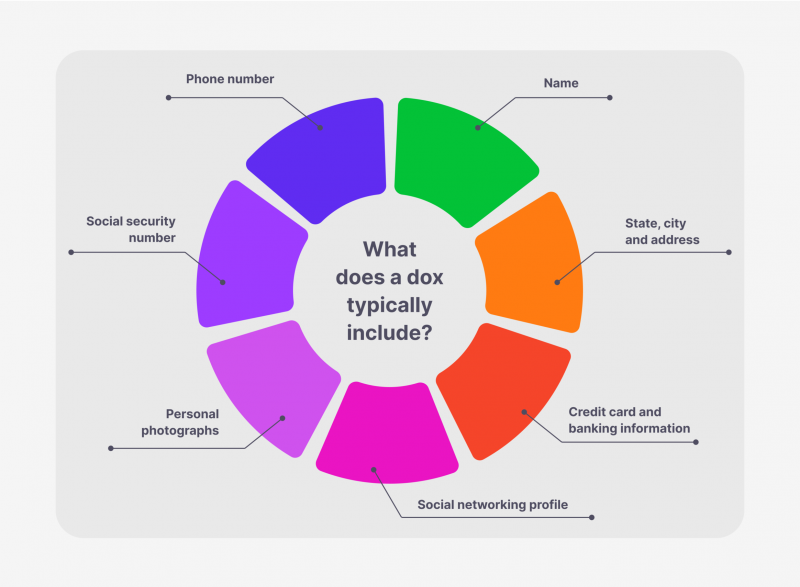
Doxers don’t just identify a person or organisation — they publish their personal and financial information, compromising material, or pass it on to interested individuals who further process and compromise it.
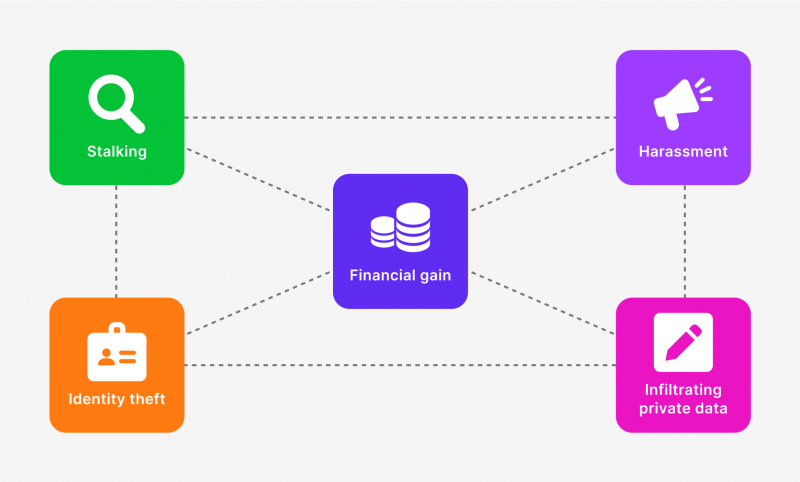
The ultimate goals of doxxing include attracting public attention, organising a violent campaign of pressure and harassment, and calling on the state or some group to use force against the victim.
How Does Doxxing Work?
Now that you know the doxxed meaning in crypto, it’s time to talk about how this process works. As mentioned above, the doxxing process involves a number of activities aimed at obtaining the necessary financial or personal information of crypto market participants for their further use. Let’s take a look at the main ones:
1. Phishing
Phishing in the crypto sphere is a type of fraud whose goal is to gain access to confidential user data — usually logins and passwords. However, the goal can also be financial data and any activity related to the trading process in financial markets.
This is achieved by sending mass emails on behalf of popular crypto brands, as well as personal messages within various services, for example, on behalf of crypto exchanges or popular services, including internal correspondence on social networks.
2. Hacking
Doxing in the crypto niche also includes classic hacking attacks that aim to obtain sensitive information of any format. In addition, their goal is to disable (disable) the software of computers and other systems (such as the infrastructure of crypto exchanges) where the data required by the attackers is stored.
Cybercriminals commonly use hacking techniques to access sensitive information, particularly through doxxing.
These techniques may include utilising intrusive code to execute zero-day exploits, disseminating viruses and malware, launching brute-force attacks, or employing other methods of password cracking. Organisations must be vigilant and stay informed about these strategies to protect their data from potential breaches.
3. Sniffing
Sniffing in the crypto environment is a process in which information security is violated as part of an organisation or individual’s unauthorised interception and analysis of network packets (data traffic).
Hackers use sniffers to steal valuable data by monitoring network activity and collecting personal information about users. Most often, attackers are interested in user passwords and credentials. This data makes it possible to gain access to accounts and, therefore, assets and funds.
The sniffing software intercepts all data packets passing through the selected network interface and displays them in a readable format for analysis. Sniffers can work both as an intermediate device, redirecting traffic from one network interface to another and in listening mode when all network traffic is collected without changing or redirecting it.
4. IP/ISP Doxxing
IP or ISP doxxing is a situation where the doxxers can obtain the user’s IP address directly linked to their physical location. Once the doxxer has the IP address, they use call spoofing apps and social engineering techniques to lure the user into a tech support scam.
The ultimate goal of this scam is to trick the user’s internet service provider (ISP) into sharing sensitive information, such as the user’s phone number, email address, date of birth, and social security number.
5. Social Media Doxxing
The practice of social media doxxing involves the collection of personal information shared on social media accounts. This information can include responses to trivia questions, which can be exploited by doxxers to potentially answer security questions and gain access to other online accounts.
It is crucial to be aware of the risks associated with social media doxxing and to take appropriate measures to safeguard personal information.
6. Spoofing
Spoofing is a cyberattack in which a fraudster impersonates a trusted source to access sensitive data or information. Spoofing can occur through websites, emails, phone calls, text messages, IP addresses and servers.
The goals of crypto spoofing can vary, but in most cases, they boil down to obtaining sensitive data or financial gain. For example, scammers can send a spoofing email, supposedly on behalf of a well-known crypto exchange, with information about lucrative offers.
The user follows the link in the email and ends up on a fake website where they are asked to enter their login and password or make a financial transaction.
According to Safehome.org’s 2022 report, more than 43 million Americans have experienced doxxing. 52% of doxxing victims reported that the attack on them was the result of an argument with strangers online, and 25% of attackers personally knew their victims.
Protective Measures Against Doxxing
Practice shows that no one is immune to Doxxing as part of standard trading activities. The likelihood of a situation in which crypto investors’ personal and financial information is compromised is determined by several factors, the presence of which determines the degree of damage caused by this practice. So, how to know if you’ve been doxxed and how to protect yourself from fraudsters become two main questions.
Protecting the IP Address with a VPN
Asking the question, “Is doxxing illegal?” one may come to believe that there is some kind of anti-doxxing law regulating this practice. Since publicly posted information offers access to all users of the crypto space, without exception, there is a dilemma about the legality of its use for personal purposes.
Nevertheless, one of the main practices to protect personal and financial data, especially when working on financial markets, is the use of a reliable VPN provider to be able to change the IP address and, consequently, the physical location.
Using Strong Passwords
This practice is a classic example of protecting personal information and confidential data. It involves the use of complex passwords, the selection of which becomes more difficult in direct proportion to their complexity (i.e. length and special characters).
Due to the use of complex passwords, it becomes much more difficult to crack even with the use of highly professional software aimed at analysing possible combinations, one of which can be a winning combination that can be used to gain access to a user account.
Using Multi-Factor Authentication
Multi-factor authentication (MFA) is a security concept that requires at least two ways to authenticate (validate) account data to establish the truth of an identity and allow access to a system. To verify identity, multi-factor authentication combines several or more factors that are not directly related, such as knowledge, possession, and property.
The goal of multi-factor authentication is to make it difficult for an attacker to gain unauthorised access to a system, network, device, or database by forming multiple layers of defence.
When one of the authentication factors is compromised, the second one comes into play, which increases the chances of blocking access. Often, such protection becomes a stumbling block for malicious intruder actions.
Hiding Domain Registration Data from WHOIS Protocol
A domain is a web resource’s unique address containing specific content. A domain allows a brand a unique name in the Internet space, the ease of finding which is determined by the brand’s popularity.
WHOIS is an application layer network protocol based on TCP protocol (port 43). Its application obtains registration data on the owners of domain names, IP addresses, and autonomous systems. The protocol assumes a “client-server” architecture and is used to access public database (DB) servers of IP address registrars and domain name registrars.
By restricting access to data packets contained in a domain, a user or crypto organisation can reduce the likelihood of doxing and other undesirable illegal phenomena.
Controlling the Amount of Publicly Available Data
Today, every company or famous person within the marketing campaign of their brand has an account on many social networks, where various kinds of information and data related to their activities are systematically published.
This practice, despite the promotion of business products and services, also becomes a tool to attract the attention of intruders who aim to get the data.
To prevent data leakage, the technique of disseminating important but, at the same time, sensitive information through closed channels or using private access technology, which can only be accessed by authenticated users of a particular resource, is used.
Conclusion
When understanding the doxxed meaning in crypto, it can be concluded that this practice is legal if the sought information is in the public domain, but has very negative consequences if such information is used for illegal purposes, which can lead to tarnished brand reputation or problems in the life of an individual crypto market participant.