When cryptocurrencies first entered the global market, their primary appeal was unprecedented freedom for users. Crypto owners could store, receive and pay virtual currencies without any supervision from third parties. However, soon the crypto’s biggest advantage became one of its most crippling weaknesses, as numerous fraud cases, money laundering, and terrorist financing cases started to show.
The Know Your Transaction (KYT) concept was developed to offset the potential threats of crypto transactions by making the payment process more transparent and secure. This article will discuss the numerous benefits of the KYT procedure and why you should consider integrating this mechanism within your business.
Key Takeaways
- The Know Your Transaction compliance tool allows companies to monitor and detect questionable crypto transactions.
- KYT enables crypto businesses to secure workflow, prevent financial crime, and maintain a tight reputation.
- KYT tools have limitations, including high setup costs, false positive cases, and user privacy concerns.
- Selecting a perfect KYT provider depends on your operating budget, business needs and the complexity of your crypto transactions.
What is KYT, and How Does it Prevent Financial Crimes?
The Know Your Transaction (KYT) compliance mechanism allows businesses to monitor transactions and possibly prevent financial crime within their transaction history.
The KYT methodology is the backbone of anti-money laundering (AML) and counter-terrorist financing guidelines (CTF). The financial transactions carry bits of information that might be hard to analyse without the KYT tools and mechanisms in place.
KYT also works with a similar compliance tool called the Know Your Customer (KYC) guideline. While KYT monitoring methodology dates back to the 1970s, this tool is constantly evolving with the changing needs of the market.
Since criminal activities in the financial sector are becoming more complex and difficult to spot, the KYT mechanism must be upgraded systematically. Naturally, KYT has become one of the most reliable tools in the crypto industry since it allows businesses to stay safe and avoid crippling losses or consequences of crime.
While some believe that KYT goes against the foundation of blockchain, it has proven to be an indispensable tool in fighting illicit activities conducted with digital assets.
How Does KYT Work?
As mentioned, the KYT tool has undergone many changes and has evolved continuously throughout the decades. However, the general purpose and methodology of KYT remain the same as they were in the beginning. Financial institutions, crypto exchanges, brokerages, and many other companies utilise this mechanism to spot suspicious fraudulent transactions, and here’s how they do it.
The AML Transaction Monitoring and Analysis
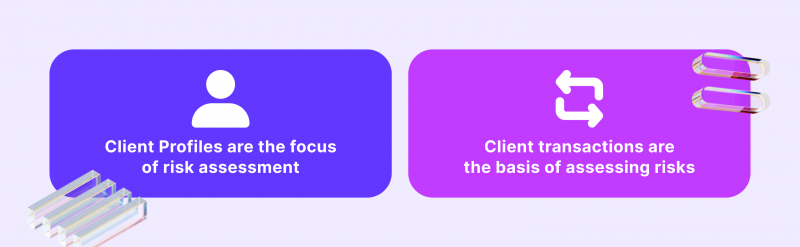
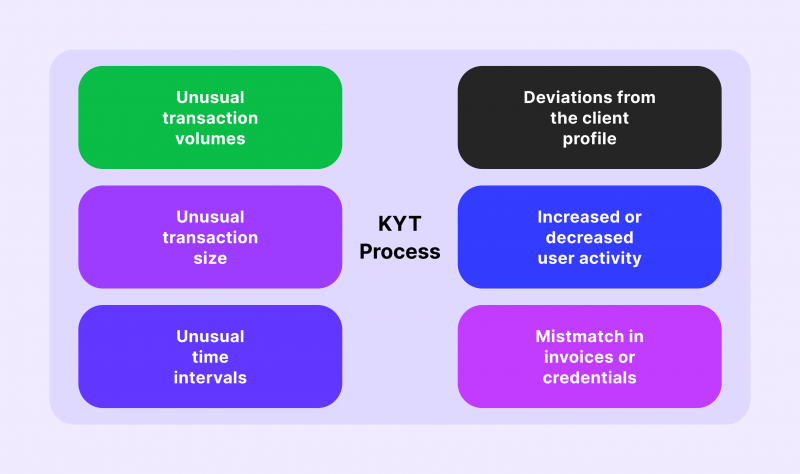
The core of successful KYT procedures is tracking and examining financial transactions. First and foremost, the KYT technology dictates that companies should gather financial transaction data, including IP addresses, recipient information, invoices, and any other available data points. The information is then processed by a complex algorithm trained to detect anomalies and deviations from the norm.
These abnormal activities might include making small transactions to a massive account, only making withdrawals, or conducting transfers in strange time intervals.
However, this is only the tip of the iceberg, as KYT algorithms have gotten increasingly advanced due to receiving frequent updates to their system. The updates are primarily empirical, taking into account the latest fraudulent crime cases and other discovered white-collar crime activities.
Evaluating Client Profiles
After gathering and analysing transactions, it is crucial to create a client profile. While it is possible to analyse transfers individually, creating a client behaviour profile is much more efficient and effective. This process allows companies to develop specific expectations for every client and reliably conclude if there is any suspicious activity going on.
For example, if a client usually conducts only several transactions with their cryptocurrencies per month and suddenly starts actively transferring funds every two days, this could be a sign of potentially malicious activity. Naturally, behaviour changes can have legitimate reasons on the client side, but it is still prudent to check any questionable deviations.
The crypto sector is ripe with individuals who start off as legitimate clients, accumulate a respectable client profile and then engage in illicit activities. So, conducting client profile assessments in real-time is important, even if the user account has been legit for a long time.
KYT and KYC methodologies have solved many high-profile crime cases, allowing authorities to capture terrorist group members by simply analysing the payment patterns across international networks.
Advantages of Employing the KYT Compliance Procedures
The KYT crypto process is invaluable for any substantial business within this sector. Currently, even small crypto businesses would do well to consider the KYT transaction procedures since the financial crime in virtual currencies is at an all-time high.
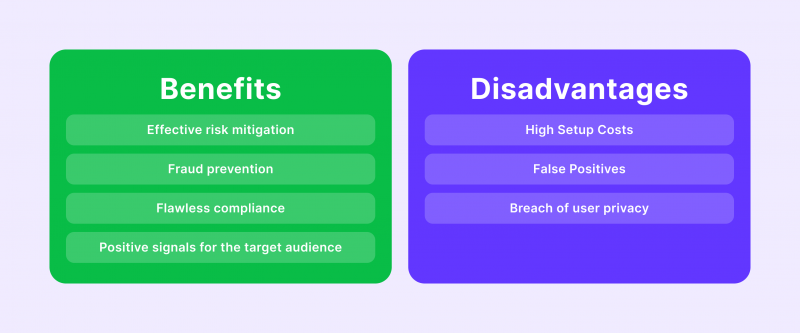
The KYT procedure prevents money laundering risk, scammer activities, terrorist or criminal financing instances and many other malicious activities conducted through financial means. Arguably, the most crucial advantage of KYT is helping businesses maintain a flawless track record and a high-level reputation in the eyes of the public.
Adopting cryptocurrency transaction monitoring tools allows companies to send out a signal that their platform is risk-free and safe for use. As a result, crypto transaction monitoring can increase revenue figures while maintaining security within your digital workflow.
Know Your Transaction Limitations
There are three main concerns related to the KYT methodology, including the setup costs, false positive risks and the dilemma of data privacy.
Firstly, the setup expenses are considerable and many smaller companies might require substantial capital investments for KYT. Implementing all relevant systems and protocols and dedicating staff hours to this process is very costly initially and relatively expensive in subsequent months.
Moreover, the KYT procedure can produce many false positive outcomes for suspicious activities. As mentioned above, there could be many cases where users simply change their behaviour for legitimate reasons. So, companies might have to spend a lot of time and resources to investigate clients who do not pose any danger to the business.
Finally, the data privacy challenges are exceptionally prominent with crypto KYT procedures. One of the primary attractions of using blockchain transactions is the anonymity and freedom of users. The KYT process naturally minimises these advantages, but the trade-off is necessary to create a safe hub for transactions and storing funds.
Critical Differences Between KYC and KYT Procedures
The Know Your Customer principle is another crucial aspect of keeping your crypto business safe. However, unlike KYT, it is more concentrated on the initial onboarding process. According to KYC, collecting customer information during the setup process is crucial in acquiring all the data.
KYT and KYC go hand-in-hand since collecting user data helps create a customer profile and check their transaction activities accordingly. It is best to combine both of these methods to achieve maximum compliance and security.
How to Acquire a Suitable Transaction Monitoring Software
The crucial steps in obtaining a proper KYT tool depend on your immediate business needs. However, there are several factors to consider in general. First and foremost, the KYT tool in question should have appropriate detection tools that can be automated. The most significant advantage of KYT software is that it automatically detects any questionable behaviour, saving businesses time and money.
The KYT solution should also be easy to navigate and monitor since your staff will spend a lot of time with this tool. Moreover, the KYT providers should update their underlying methodologies frequently. This way, the software will have methodologies to detect new and emerging malicious activities on the market.
Finally, the pricing matters as some KYT providers charge a hefty price tag for their subscriptions. However, smaller companies often do not require the extensive and complex services of large KYT providers. So, before committing to any choice, analyse your needs, business scope and operational challenges well since it might save you a lot of monthly expenses.
Final Thoughts
The KYT process is necessary for any crypto company that aims to preserve a flawless reputation and ensure security in its operations. Analysing client behaviour and blockchain transactions is a great way to stay compliant, take care of your stakeholders and prevent irreparable losses. So, it is advisable to analyse the market and select the perfect KYT provider for your needs. This tool might save your company one day from unforeseen and dire consequences.