Cryptocurrency continues to attract millions of users due to its decentralized nature and high-return potential. However, with its rise, a new type of threat has emerged—crypto wallet drainers. These malicious programs target unsuspecting users, emptying victims’ crypto wallets in seconds. As cryptocurrencies become more mainstream, understanding how these threats work and how to stay secure is crucial.
This article will explore what crypto wallet drainers are, how they operate, real-world examples of attacks, and, most importantly, how you can protect yourself from falling victim to such scams.
What Are Crypto Wallet Drainers?
A crypto wallet drainer is a type of malware specifically designed to target digital cryptocurrency wallets. These drainers trick users into giving access to their wallets, siphoning off funds, and often exploiting vulnerabilities in the wallet’s security protocols or decentralized applications (dApps). While some crypto drainer scams are simple, others are sophisticated, blending phishing and malicious smart contracts to deceive even experienced users.
A well-known incident occurred on December 17, 2022, when scammers used a fake website to trick an NFT collector into licensing their Bored Ape NFT. Once the user signed a malicious contract on the blockchain platform, the scammers gained access to 14 NFTs worth over $1 million, transferring them from the victim’s wallet.
Crypto wallet drainers are prevalent across the Web3 ecosystem. They often target wallets through fake websites, phishing links, or counterfeit decentralized applications, luring victims into approving transactions that hand over control of their assets.
Types of Crypto Wallet Drainers
There are several methods used by wallet drainer perpetrators to steal digital assets:
- Phishing Scams: Attackers pose as legitimate entities and trick users into providing sensitive information, such as private keys or wallet details. The attackers then use this information to drain the wallets.
- Ice Phishing: A deceptive method where attackers convince users to sign fraudulent transactions that unknowingly grant them control over tokens. Ice phishing accounted for a significant percentage of crypto thefts in 2023.
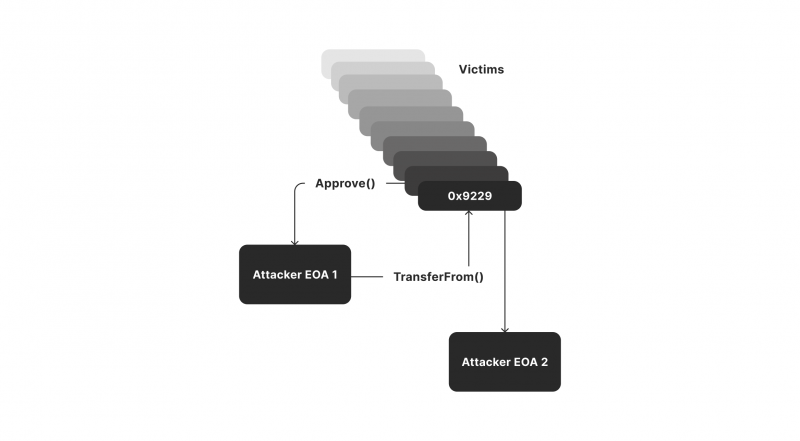
- Malicious Smart Contracts: Some attackers disguise malicious contracts as part of legitimate transactions. When a user interacts with the contract, they unknowingly grant access to their wallet.
- Fake Airdrops and NFT Drops: Scammers often lure victims by offering free NFTs or cryptocurrency airdrops. Once users connect their wallets, their funds are siphoned off.
These tactics have proven devastating, as demonstrated by several high-profile cases. For example, in the Inferno Drainer campaign, over $81 million was stolen from 134,000 victims using phishing techniques, highlighting the severe impact of these crimes on the crypto community.
How Do Crypto Wallets Get Drained?
Crypto wallet drainers leverage various tactics to gain control over a user’s wallet. One common strategy involves setting up fake websites that mimic legitimate cryptocurrency platforms. Users visiting these sites are prompted to connect their wallets for tasks like NFT minting or airdrops. Unknown to them, these connections facilitate the transfer of their funds to the attackers’ wallets.
Another approach involves malicious dApps, which exploit smart contract vulnerabilities. Users may unknowingly approve a transaction through these dApps, allowing attackers to withdraw funds. Once the malicious transaction is signed, the damage is irreversible, as blockchain transactions are final.
Moreover, scammers use platforms like social media and search engine ads to promote fraudulent websites. Users who click on these links often find themselves on a counterfeit site, where any interaction with their wallet results in the theft of their assets.
Examples of Crypto Wallet Drainer Attacks
Several notorious campaigns have made headlines due to the substantial losses they caused:
- Venom Crypto Drainer: As of February 2023, Venom drained over 15,000 wallets, stealing $27.5 million in assets. The campaign targeted multiple brands, including Metamask and Trust Wallet.
- Inferno Drainer: This campaign stole over $29 million from 70,000 victims using fake NFT airdrops.
- Pink Drainer: Known for using social engineering tactics, Pink Drainer attacked Discord servers, leading to $3 million in stolen assets.
These incidents highlight the growing sophistication of crypto wallet drainers and their ability to bypass traditional security measures.
The Impact of Crypto Drainers
Crypto wallet drainer scams are causing significant financial losses worldwide. According to a study, more than 320,000 users were affected by these scams in 2023 alone, leading to nearly $300 million in losses. In some cases, a single attack resulted in millions being stolen, such as the theft of over $24 million in one transaction.
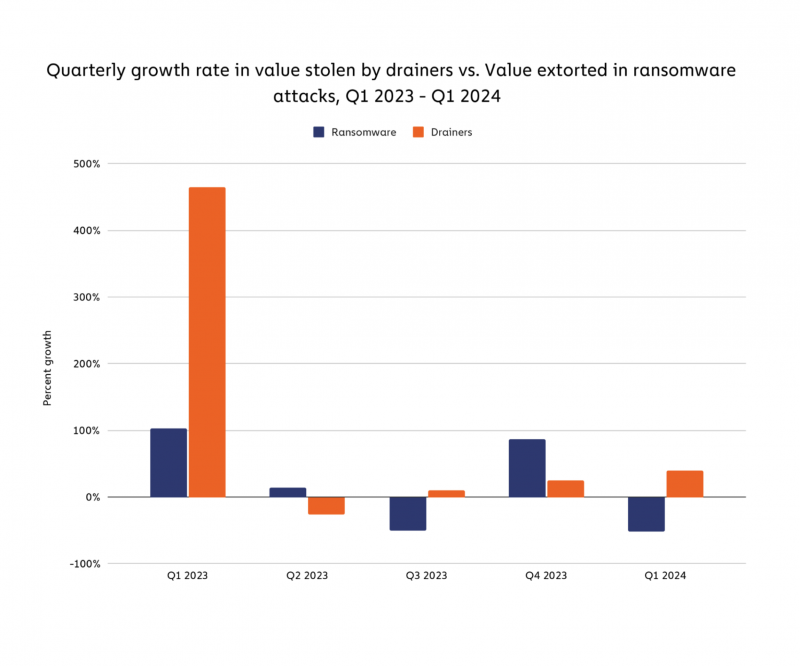
Beyond the immediate financial impact, these scams erode trust in cryptocurrency platforms, deterring new users and casting doubt on the security of decentralized finance (DeFi). As the value of stolen assets grows, so does the appeal for cybercriminals to target the crypto ecosystem.
How to Avoid Crypto Wallet Drain
To avoid falling victim to crypto drainer scams, it is essential to follow robust security practices:
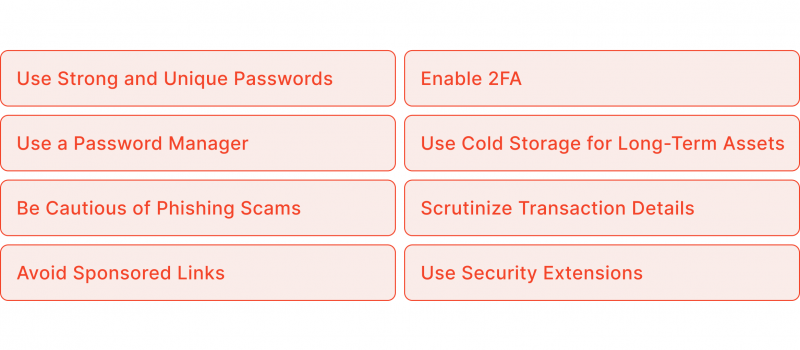
- Use Strong and Unique Passwords: Create strong and unique passwords for each of your online accounts, particularly those connected to your crypto activities. Avoid using the same password across multiple accounts.
- Enable Two-Factor Authentication (2FA): Ensure that 2FA is enabled for all your accounts, adding an extra layer of password protection.
- Use a Password Manager: Managing multiple accounts can be challenging, but a password manager can securely store your credentials, generating strong and unique passwords for each site.
- Cold Storage for Long-Term Assets: Keep the majority of your funds in cold wallets (hardware wallets not connected to the internet), and only use hot wallets (online wallets) for day-to-day transactions.
- Be Cautious of Phishing Scams: Be vigilant when dealing with unexpected emails, messages, or links. Always verify the source before clicking on any link, and avoid sharing private keys or passwords.
- Scrutinize Transaction Details: Always double-check the details before approving a transaction. Malicious actors often use slightly modified addresses that closely resemble legitimate ones.
- Avoid Sponsored Links: Avoid clicking on sponsored links in search engine results. These links can lead to fake websites designed to steal your credentials.
- Use Security Extensions: Web3 security extensions, such as Wallet Guard, can help identify phishing pages and assess the risks associated with interacting with dApps.
- Update Software Regularly: Keep your wallet apps, browsers, and mobile devices updated with the latest security patches to reduce vulnerabilities.
Following these measures can significantly reduce your exposure to crypto wallet drainers and avoid online scams.
What to Do if Your Wallet Has Been Drained
If you suspect your wallet has been compromised, immediate action is critical:
- Audit Your Transaction History: Regularly review your transaction history for unauthorized activity. Suspicious or unknown transactions can be a red flag that your wallet has been compromised.
- Revoke Suspicious Permissions: Use tools to audit and revoke access to suspicious dApps or contracts connected to your wallet.
- Report the Incident: Notify platforms like Etherscan to flag malicious addresses and prevent further attacks. You should also report phishing sites to their domain providers and flag stolen NFTs on marketplaces like OpenSea.
- Consult Security Experts: If necessary, seek advice from cybersecurity experts to help identify the source of the compromise and secure your assets.
- Transfer Remaining Funds: If possible, transfer any remaining funds to a secure wallet while ensuring that malicious scripts are not triggered in the process.
Taking these steps promptly can help mitigate further losses and prevent the attackers from accessing additional funds.
Final Takeaways
Crypto wallet drainer scams are becoming increasingly sophisticated, with attacks targeting users of all experience levels. To stay secure, it is crucial to adopt best practices for password protection, use multiple accounts, and secure your crypto assets in offline wallets.
By staying informed about the latest crypto drainer scams and implementing strong security measures, you can protect yourself from these growing threats and continue engaging with the cryptocurrency ecosystem confidently.
With vigilance, proper security protocols, and an understanding of the risks, crypto users can outmanoeuvre a wallet drainer and keep their digital assets safe.